The Path to Trusted Software
3 Keys to Securing Applications in the Age of AI

Welcome to the new reality of Application Security
The idea that every company is a technology company is not new, but it is more true than ever. With 70% of top economic performers using their own software to differentiate1, fast development and delivery of applications translates to a competitive edge. But while organizations churn out applications to create efficiencies, improve customer experience, and speed new offerings to market, the imperative for fast innovation presents not only incredible opportunities but also a new set of challenges for CISOs and their Application Security teams.
As businesses, government organizations, and NGOs shape their futures, the number of developers continues to rise - with a 75% growth predicted for this decade2 - along with the number of applications these developers build and deploy at speed.
At the same time, securing these applications is more urgent than ever. Complex software supply chains make it hard to protect the full attack surface, and zero-day attacks require quick and comprehensive action. Security reporting and compliance requirements also create new challenges for managing security practices at scale. Cybersecurity Ventures predicts that the global cost of software supply chain attacks on businesses will reach nearly $138 billion by 20313. Under these pressures, it is not surprising that Cybersecurity is the #1 ranked risk to business globally in 2024, according to the IIA4.
The rise of AI amplifies the need to modernize
Application Security
The rapid adoption of AI-gen code for software development is not only creating opportunity but also magnifying risk. AI innovation is compounding the acceleration of code delivery, while governance is playing catch-up. In a recent survey of developers and application security professionals, 91.6% of respondents said that AI coding tools generated insecure code suggestions at least some of the time. Yet, less than 10% have automated the majority of their security checks to keep up. And worse, 80% of respondents said that developers in their organizations bypass the AI security policies that were meant to help manage risks5.
In this new reality of not only more developers, but also higher code-to-developer output - risks are rising, and AppSec teams are increasingly charged with bridging the gap between development and security organizations to develop fast and stay secure.
Understand the best practices for securely adopting AI in your development process. Download our guide on secure AI integration
CISOs and their Application Security organizations must plot a new path to trust software at full speed and innovate without limits. To do this, they need these three keys …
K E Y # 1 :
Think “Developer Security,” not “Application Security”
Applications are only as secure as the code they are built on. Developers are at the front lines of preventing and fixing vulnerabilities in code before they introduce business risk, and the only application security solution that works is one that’s actually used. This means that Application Security must be approached as Developer Security.
When AppSec teams prioritize a secure code-to-cloud developer experience, they are putting security tools in the hands of developers to quickly secure both human and AI-gen code from the start. More successfully securing applications than legacy AppSec approaches, Developer Security will
Act like a developer tool - Seamless integration across the software development lifecycle (SDLC), for a focus on actionable fixes, rather than simply finding vulns
Boost productivity - Full IDE immersion, with AI-powered fixes to simply validate and merge - for fast remediation;
Make coverage matter - Breadth of coverage across the application lifecycle and the software supply chain, for tool consolidation and efficiency gains; and
Provide Gen AI guardrails - Separation of tools that generate code from those that check code - critical for security best practices.
“Shift-left security” is not a new notion - and refers to aligning modern DevOps practices by securing code through continuous integration and continuous development (CI/CD). However, enterprises building their future on innovation know that legacy Application Security tools must become a thing of the past - with their long, often costly implementations and clunky usability for developers.
Given increased pressure to ship code quickly, plus the rapid adoption of gen AI tools to increase development velocity, a successful AppSec solution must walk, talk, and quack like a dev tool, empowering developers with the knowledge, resources, and technology needed to identify, understand, and mitigate security vulnerabilities within their code in real-time.
Equip your team with the essential SAST best practices.
Download our cheat sheet for secure, efficient code development.
Yet, Developer Security must also provide security depth and sophisticated management capabilities for AppSec Teams, which brings us to governance.
K E Y # 2 :
Overlay DevSec Governance for Scale
With developer buy-in achieved, organizations must make sure DevSec governance capabilities are in place to scale their ability to secure applications at the speed of AI. With AppSec teams at the forefront of bridging the gap between development and security functions within an organization, the right governance tools are integral to ensuring trusted software and driving innovation.
A modern DevSec Governance structure will include:
Smart policies - that identify and define actions to prevent or remediate actual business risk, against vectors beyond severity, including OS License Compliance
Comprehensive controls - to easily map fixes to the development teams responsible
Ecosystem support - with AppSec-governed integrations that bring prioritized risk back to the developer to prevent and remediate; witO
Enterprise analytics - to manage accountability and reporting.
With DevSec Governance in place, a Developer Security solution exists within the security stack, procured and managed by the AppSec teams that require full visibility, controls, and management capabilities - as well as the ability to prioritize which vulnerabilities must be addressed first, and which do not require action. This brings us to the third key.
Stay ahead of the curve with our DevSecOps Playbook. Learn how to integrate security seamlessly into your DevOps pipeline
1 McKinsey Digital: “Every company is a software company: Six ‘must dos’ to succeed” (2022)
2 Forbes: “Rising Stars Of The Tech World: Why Developers Are Job Market Royalty” (2021)
3 Snyk:”2023 Sofware Supply Chain Report”(2023)
4 Internal Audit Foundation: “Risk in Focus Survey Results” (2024)
5 Snyk: “Buyer's Guide for Generative AI Code Security” (2024)
K E Y # 3 :
Don’t fix vulns - manage risk
Lastly, with governance tools in place, the path to trusted software is realized with holistic application risk management, or the ability to expose actual risks, so that an organization can focus remediation and prevention efforts where they are most needed.
The rise of Application Security Posture Management (ASPM) solutions is indicative of a significant need for AppSec teams to prioritize risk management over a “find and fix” approach to application security. However, organizations should steer clear of those who are simply aggregating signals for vulnerability management, prioritized by severity alone for example, rather than leveraging complete business context to point AppSec focus and Developer remediation time toward results that matter.
Holistic application risk management requires
Full visibility - of the application landscape, through complete application discovery;<
AI-driven risk scoring - providing sophisticated context that goes beyond reachability and severity,<
Actionable evidence - graphs that visualize the criticality of each risk;<
Expansive view of controls - from AST and policy management to compliance standards to training - highlighting where security gaps may exist; plus<
Clear reporting - with and tracking of aligned coverage and focus between AppSec and Development.
While all of these capabilities will set AppSec teams on the right path toward their goals of reducing overall application risk, the solution that delivers them must also continue to adhere to the principles of Developer Security - to streamline the work of development organizations to drive efficiency, adoption, and the ability for any organization to speed to market the applications that will drive its future success.
Holistic risk management will unify the organizations that ladder up to CISOs, CTOs, and CIOs alike toward a common goal: trust software at full speed.
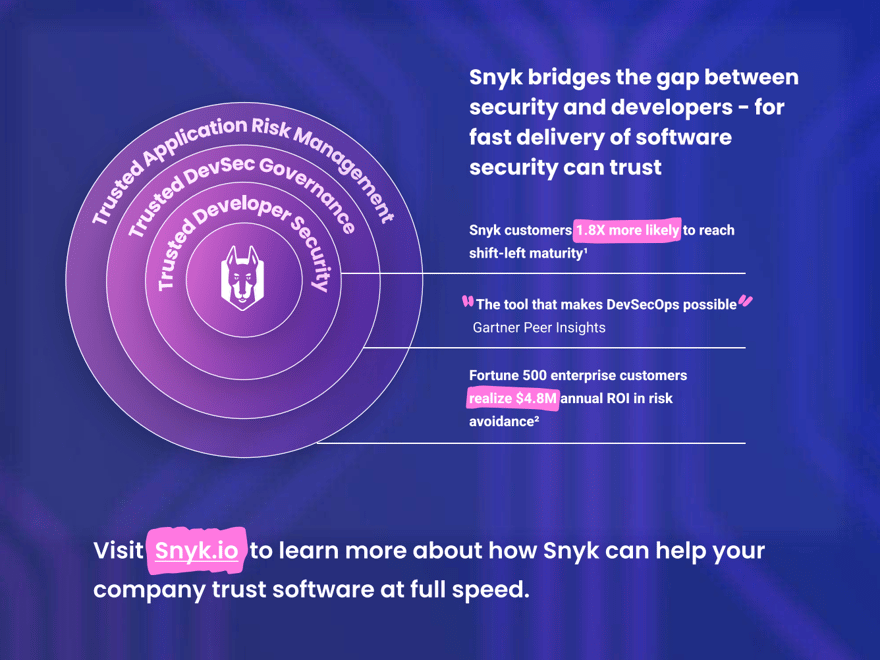
A B O U T S N Y K
a generational partner helping enterprises to develop fast and stay secure.
Snyk is the pioneer of shift-left developer security, a leading-edge approach to application security that helps companies around the globe forge a new path to trusted software.
Snyk unites application security and development teams with an enterprise-grade platform, helping its customers to clearly see the entire application risk landscape, prioritize what needs fixing – and what doesn’t, and prevent risk from the start with actionable remediation. Developer-loved and security-trusted, Snyk solutions serve more than 3,000 customers in 76 countries, including one out of three Fortune 50 companies. Snyk has been named a leader in the 2023 Gartner Magic Quadrant for Application Security, as well as the Forrester Wave for Software Composition Analysis.
Related Articles
Join The GBI Impact Community
Sign up to make an impact and hear about our upcoming events
By registering anywhere on the site, you agree with our terms and privacy policy