Too hot to handle: Why modern work has given rise to HEAT attacks
A deep dive into how modern work has given rise to Highly Evasive Adaptive Threats (HEAT)
The cyberthreat landscape is a changing beast that knows no end. In the blink of an eye, any one of the thousands of cyberthreats – old or new – is crowned the attack du jour that security teams need to prepare for. Just keeping up with these threats is an exhausting and daunting responsibility, given the acceleration of digital transformation initiatives that have catapulted users, data, and business-critical applications to the cloud. Let’s face it, today’s enterprise network offers tremendous scale and opportunities for businesses, but even more promise for threat actors.
The single biggest problem in security today is the legacy approach a majority of organizations take to protect these networks from a strategic and technological standpoint – one that’s cemented in detecting and responding to cyberthreats. As we all know too well, security practitioners are easily distracted by shiny objects that come in the form of new technology that claims to prevent the latest headline-grabbing breach. And if you take into account some of the biggest breaches of the last five years alone, they have one common theme: ransomware. The rise of ransomware has taken center stage for the last decade, ravaging global businesses, government agencies, and everyday citizens around the world.
Apart from the devastating and long-lasting effects ransomware can have on organizations, perhaps the bigger issue is that despite all these cybersecurity efforts, ransomware still finds its way through traditional defenses.
Today, organizations dread the day when a ransom request finally hits end-user screens, and they prepare for it by backing up data centers in the hope of retaining control of their sensitive information. Ransomware is the shiny object getting our attention. But we’ve lost focus on the areas that allow the attack to occur in the first place.
Ransomware takes center stage
Ransomware attacks are considered a defining era for cybersecurity, and it’s the fastest-growing type of cybercrime that impacts all businesses, consumers, and devices. Since 2016, there have been 4,000 ransomware attacks daily in the United States, according to a report by the U.S. Department of Justice. Estimates by Cybersecurity Ventures point to ransomware impacting businesses every 11 seconds in 2021, and the frequency of attacks is projected to accelerate to every 2 seconds by 2032. That could equate to $20 billion in costs associated with ransomware in 2021, and up to $265 billion in 2031.
Let’s not forget how a majority of these attacks initially kickstart: phishing messages. According to Verizon’s 2021 Data Breach Investigations Report (DBIR), phishing is the top “action variety” seen in breaches in the last year. Additionally, 43 percent of breaches involve phishing and/or pretexting. Roughly 96 percent of these phishing messages tend to arrive by email – the lifeblood of modern enterprise communication – and feature malicious PDFs and Microsoft Office files. They are the delivery vehicles of choice for today’s threat actors since these types of files are universally known and trusted in the modern workplace.
As these attacks continue to ravage businesses, government agencies, and everyday people globally, threat actors are not letting up. If an attack tactic works for cyber miscreants, they tend to stick with it, and that’s been the case with ransomware. Threat groups such as Darkside, Nobelium, Conti, and the now defunct REvil have been successful time and time again, leading to millions of dollars in profit for them. To put it into perspective, the average ransom demand associated with these attacks is $200,000.
And it’s not just sophisticated threat groups that are in on the digital assaults. Thanks to ransomware as a service (RaaS), a subscription-based model that enables buyers to leverage already developed ransomware tools to launch attacks, 60 percent of ransomware attacks analyzed by security firm Sophos were attributed to RaaS groups.
From 2019 to 2020, an analysis by the Washington Post found that ransomware attacks more than doubled – and that’s before Pandora's box truly opened up. After the COVID-19 global pandemic hit, a perfect storm was created that opened digital doors for threat actors and created an evolution in the threat market.
The perfect storm: The rise of Highly Evasive Adaptive Threats
When entire workforces worldwide went remote in 2020, organizations were able to pivot quickly to a new business model by migrating apps and services to the cloud so any employee armed with a web browser ostensibly could access what they needed to do their jobs anytime, anywhere. The office essentially became the browser, opening a world of resources to those who work remotely. Since then, Google has reported that end users spend an average of 75 percent of their workday using a web browser.
Additionally, there’s been an explosion of Software as a Service (SaaS) applications as remote and hybrid work have become the norm. Recent research indicates that by the end of 2021, 99 percent of organizations will be using one or more SaaS solutions, and nearly 78 percent of small businesses have already invested in SaaS options.
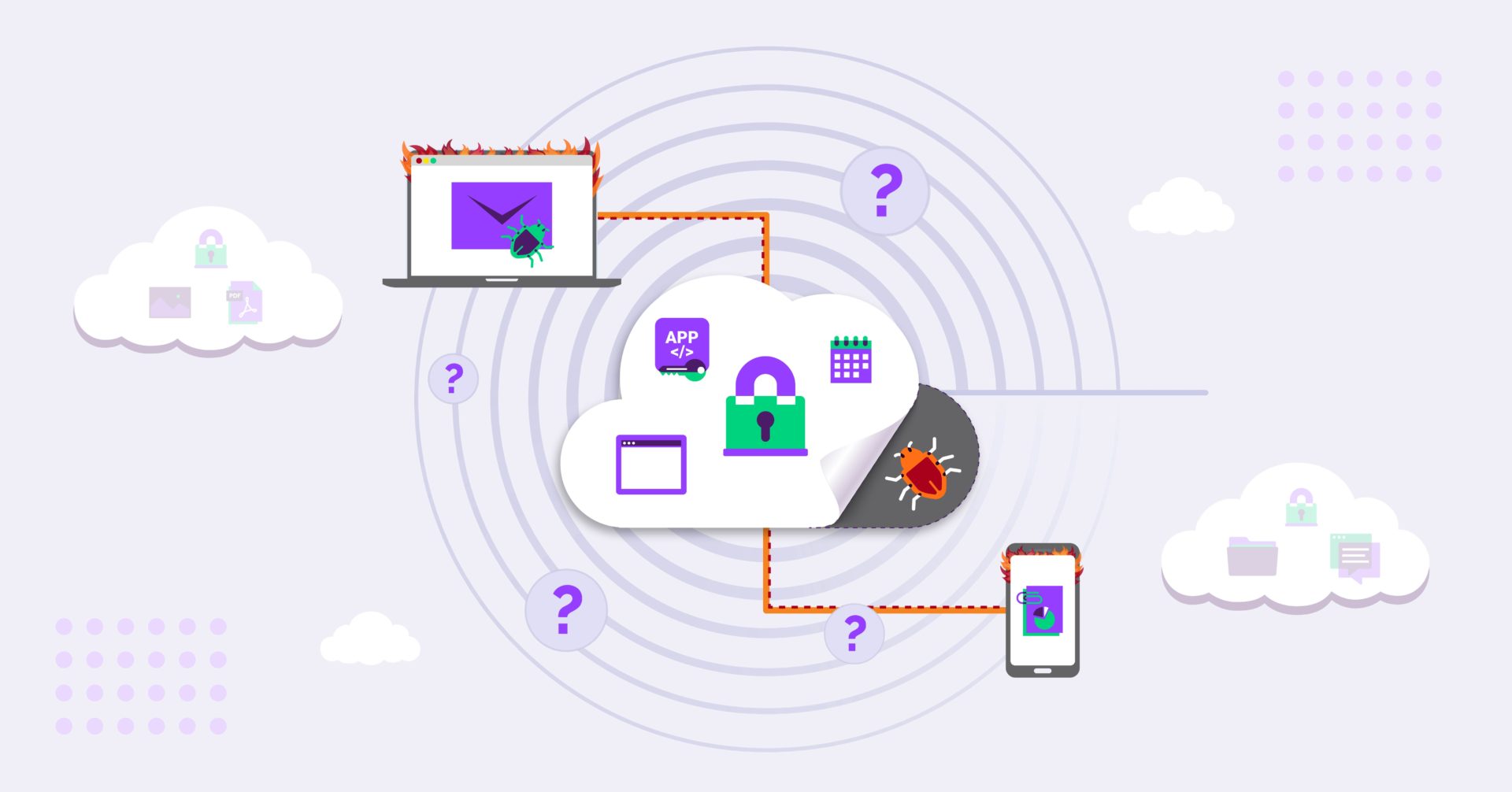
Today users, their data, and applications are all found in the cloud. While all this work is being conducted in the cloud, it’s also the one place where traditional security measures – which are still very much relied on today – aren’t located. With web browsers constantly being updated to address vulnerabilities, and SaaS applications further expanding the attack surface, there is more distributed work – and data – to protect. Threat actors understand this paradigm shift and have adapted by creating Highly Evasive Adaptive Threats (HEAT), which are used as beachheads for initiating ransomware, extortionware, and other endpoint breaches.
HEAT attacks are actively being leveraged by well-known threat groups such as Nobelium, the Russian state-sanctioned outfit behind the SolarWinds supply chain attack in 2020 and thousands of others from July to October of 2021 alone. Then there’s the Gootloader campaign, another classic example of a HEAT attack that leverages SEO poisoning to generate high-level page rankings for compromised websites. This particular campaign is known to deliver the REvil ransomware.
What’s bringing the HEAT?
A HEAT attack is a class of cyberthreat that leverages web browsers as the attack vector and employs various techniques to evade multiple layers of detection in current security stacks. Consequently, HEAT-based attacks bypass traditional web security measures and leverage web browser features to deliver malware or to compromise credentials. In many cases, this leads to the delivery of ransomware.
After analyzing more than half a million malicious URLs, the Menlo Labs team determined that 69 percent of them leveraged HEAT tactics. Additionally, the team observed a 224 percent increase in HEAT attacks in the second half of 2021.
Threat actors are able deliver malicious content to the endpoint by adapting to the targeted environment, rather than coming up with new tools. As seen in recent web-borne threats, attackers are taking advantage of legitimate features and tools available within browser environments to deliver malicious payloads to the endpoint. A perfect example is the Astaroth banking Trojan, which makes use of HTML smuggling to sneak malicious payloads past network-based detection solutions.
Historically, Astaroth has been known as a threat that lives off the land, which means that once it’s executed on the endpoint, it leverages legitimate tools and programs available within the endpoint to carry out malicious actions. The Astaroth actors have now taken one more step above the endpoint – to apply the same tactic on browsers by using HTML smuggling, which takes advantage of legitimate HTML5/JavaScript features to smuggle malicious payloads to the endpoint. This new tactic illustrates that modern threats are adapting to the target environment.
The velocity, volume, and complexity of HEAT attacks have increased in recent months as bad actors exploit the recent shift to remote working that has blurred the lines between business and personal computer use. And when you consider network security over the last decade, the only real advancement was the sandbox – a tool that is completely obsolete when it comes to HEAT attacks. Why? Because it relies on operating system–level activities to monitor and identify malicious content.
HEAT attacks are constructed in a way that bypasses various layers in today’s traditional security stack. They’re able to easily penetrate these layers, arrive at the web browser, and are executed to land at the endpoint or in front of end users. HEAT attacks render a decade or more of security technology investment completely ineffective.
The failures of today’s security stack
With HEAT attacks, all security defenses in action prior to arriving at the browser itself are helpless. This includes file inspections performed by Secure Web Gateway (SWG) anti-virus engines and sandboxes, network and HTTP-level inspections, malicious link analysis, offline domain analysis, and indicator of compromise (IOC) feeds. HEAT attacks evade all of these traditional methods of detection, rendering a decade or more of technology investment for enterprises totally ineffective. However, because all HEAT characteristics have legitimate uses, organizations cannot rely solely on the ability to block them; instead, organizations need to be able to prevent malicious use of the technique.
Endpoint security can’t be relied on to make up for the shortcomings of web security. Although there may be a booming endpoint detection and response (EDR) market that offers enhanced capabilities, protection against HEAT attacks isn’t guaranteed. Endpoint security can only detect a threat once it makes it onto the endpoint. By then, you must assume that your network has been compromised – all of it. Endpoint security also can’t protect against the infection of unmanaged devices, and can result in a high volume of alerts that Security Operations Center (SOC) teams must investigate, resulting in alert fatigue.
Today’s security architecture should still provide in-depth defenses, but all components of the architecture must work in synchrony to offer complete and seamless protection benefits to the organization. In recent years, network security capabilities have become less effective, putting more pressure on the endpoint and the SOC. By introducing preventative measures into the network security stack across major communication vectors, organizations greatly benefit from less pressure on endpoint compromises, as well as fewer alerts for SOC teams to investigate and escalate.
Infection vectors: What makes it a HEAT attack?
To be classified as a HEAT attack, the threat must leverage one or more of the following four evasive techniques that bypass legacy network security defenses:
- Evades both static and dynamic content inspection
HEAT attacks often use HTML smuggling and/or JavaScript trickery within browser environments to deliver malicious payloads to endpoints. This technique constructs the malicious file at the browser with no request for a remote file that can be inspected, consequently transferring the malware and effectively bypassing various firewalls and network security solutions, including sandboxes and anti-virus in legacy proxies. Moreover, file types assumed to be blocked by SWG policies can still make it to endpoints without any user interaction.
The Menlo Labs team has conducted extensive analysis of the skyrocketing use of HTML smuggling by threat actors. In one recent case, the team observed a new campaign dubbed ISOMorph, which used the popular Discord messaging app to host malicious payloads. The campaign leveraged the “downloadable BLOB” tactic to construct a file at the browser and download it to the endpoint with no user intervention. This campaign’s reach was extensive, given that Discord has more than 300 million registered users to date.
- Evades malicious link analysis
HEAT attacks evade malicious link analysis engines that are traditionally implemented in the email path, where links can be analyzed before arriving at the endpoint user. In a HEAT attack, users are targeted (or speared) with malicious links via communication channels outside of email, such as social media and professional web networks, collaboration applications, SMS, shared documents, and more. These malicious links are increasingly used to steal corporate credentials instead of personal ones in order to deliver malware to corporate endpoints, and consequently to bypass corporate security.
In a recent cyberthreat campaign, attackers leveraged spearphishing tactics on business professionals on LinkedIn. Through the platform’s direct messaging feature, attackers presented fake job offers using malicious links to ultimately infect users with a backdoor Trojan that gave attackers complete remote control over the victim’s computer. This spearphising attack never appeared in the email path and evaded any analysis that would have occurred there.
When an attack is combined with HTML smuggling, a sandbox that analyzes files and content being downloaded is blind to the potential risk. The sandbox detects and analyzes the HTML page, but does not see the dynamic generation of a file within the browser once it’s past the network security control point.
- Evades offline categorization and threat detection
HEAT attacks evade web categorization by using benign websites, either by compromising existing benign sites or creating new ones – what the Menlo Labs team has coined as Good2Bad websites. Once threat actors decide to activate these websites, they use them for malicious purposes for a short amount of time. They then revert the websites to their original content or simply remove them.
The Menlo Labs team has observed an increase of more than 137 percent of Good2Bad websites from 2020 to 2021, and an even greater increase from 2019 to 2021 – 958 percent. Given that malicious websites have short lifespans, they evade website analysis and categorization and appear as indicators of compromise (IOC) only when it is too late and already irrelevant.
Additionally, the recent critical Internet zero-day attack discovered in Log4j, a Java library for logging error messages in applications, can only increase the exploitation of good websites. Given the volume of websites that leverage Log4j, threat actors will take advantage of the increased opportunity to further compromise sites and use them for malicious purposes.
On a similar note, Menlo Labs has investigated an active threat campaign dubbed SolarMarker, which employs SEO poisoning. The campaign started by compromising a large set of low-popularity websites that had been categorized as benign, and then infected these websites with malicious content. Threat actors then artificially increased the ranking of these websites, resulting in malicious content being delivered to a large number of users. All the accesses to these websites were granted by SWGs before any offline analysis engine categorized the websites as malicious.
SolarMarker is a perfect example of a supply chain attack, in which threat actors take advantage of vulnerable websites to launch their campaigns. In this case, attackers found ways to exploit the increase in browser usage, in addition to the increase in usage of cloud-based applications by companies.
- Evades HTTP traffic inspection
In HEAT attacks, malicious content – such as browser exploits, crypto-mining code, phishing kit code, and images impersonating known brand logos – is generated by JavaScript in the browser by its rendering engine, making any detection technique prior to the web page execution or rendering useless.
Menlo Labs has observed that the top three impersonated brands for malicious purposes are Microsoft, PayPal, and Amazon.
Top 3
- Microsoft
- 462 sites created per day
- Every 3 minutes, a new Microsoft phishing website is created
- PayPal
- 187 sites created per day
- Every 8 minutes, a new PayPal phishing website is created
- Amazon
- 168 sites created per day
- Every 8.5 minutes, a new Amazon phishing website is created
Consequently, such HEAT attacks avoid detection by any static signatures that examine web page source code and HTTP traffic. Obfuscated JavaScript is often used, which increases the challenge for both security researchers and detection engines.
Since JavaScript is a ubiquitous client-side scripting language used by nearly all websites, threat actors will, naturally, use it to their advantage. Recent analysis by the HP Threat Research team uncovered a threat campaign that leveraged similar JavaScript obfuscation to deliver remote access Trojans to siphon sensitive data and gain control over infected devices. The JavaScript loader dubbed RATDispenser used JavaScript attachments, which have low detection rates.
Staying cool: Preventing HEAT attacks
The infection vectors of HEAT attacks have been plaguing organizations for years, but given the recent evolution of the threat market resulting in part from accelerated cloud migration and the proliferation of remote work, these attacks pose the greatest threat for enterprises today. As mentioned before, all traditional security capabilities – including Secure Web Gateways, sandboxing, URL reputation, and filtering – are rendered ineffective against HEAT attacks. The challenge is that because HEAT characteristics have legitimate uses, simply blocking them won’t work. Preventing the use of these techniques altogether is key.
Knowledge workers have a tremendous reliance on web browsers to remain productive. Since that’s where work takes place, that’s where the biggest security threats will lie going forward. But one thing is certain – a majority of security stacks today cannot protect against these threats.
Modern businesses will need to go beyond their current comfort level when it comes to their approach to cybersecurity, and this means questioning their long-held tenets surrounding web security – which as we’ve outlined, haven’t changed much for the last decade. Security strategies that are founded solely on the notion of detecting and remediating threats have already accepted defeat. Organizations must lead with threat prevention
Securing modern work requires modern security. Coupled with in-depth defense measures, today’s preventative security measures involve taking a Zero Trust approach to security that protects productivity where it occurs. That’s why enterprises today are increasingly adopting the Secure Access Service Edge (SASE) framework, which features key security technology components that cater to today’s remote and hybrid workforces.
Security is most effective when it is applied close to the user, application, and data. SASE essentially converges the connectivity and security stacks and moves them to the edge. In practical terms, SASE takes the entire legacy security stack that once lived inside many appliances in the data center or in branch locations on the perimeter and puts it into the cloud as a converged, integrated stack – what we like to call SASE Security.
The combination of SASE Security and a Zero Trust mindset – which ensures that all content is suspect and is subject to enterprise security controls – results in a truly preventative approach to security that addresses the legacy flaws of today’s network security stack and ultimately changes outcomes.
Related Articles
Join The GBI Impact Community
Sign up to make an impact and hear about our upcoming events
By registering anywhere on the site, you agree with our terms and privacy policy